Vistaar
Vista Guru
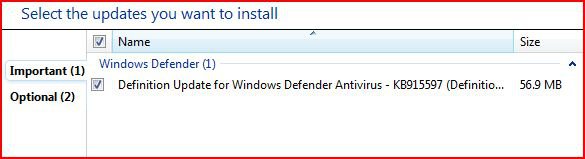
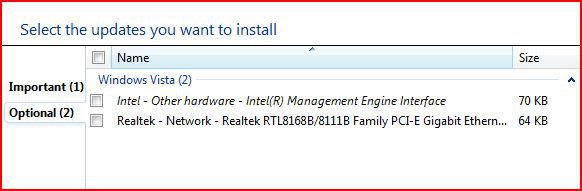
The vulnerability is CVE-2019-0708, which apparently affects every version of Windows from Windows XP to Windows 7. Microsoft has released security updates for every affected version of Windows, including Windows XP and Server 2003 - unless you believe that Windows Vista SP2 and Windows Server 2008 SP2 are different versions of Windows, in which case Microsoft did NOT issue an update for Vista. However, if you are familiar with the MSFN thread Server 2008 Updates on Windows Vista, then you know that Vista can be patched against this threat if anyone so desires. Edit: Today (May 23, 2019) Microsoft updated Customer guidance for CVE-2019-0708 | Remote Desktop Services Remote Code Execution Vulnerability to include Windows Vista at the bottom of the list. The link for 4499180 takes you to the May 2019 Security Only Quality Update for Windows Server 2008!?  Furthermore, the KB article was updated yesterday (May 22), and contains this Notice: "This security update can be installed on Windows Server 2008 Service Pack 2 and on Windows Vista. "
Furthermore, the KB article was updated yesterday (May 22), and contains this Notice: "This security update can be installed on Windows Server 2008 Service Pack 2 and on Windows Vista. "  Microsoft is not just admitting that updates for Server 2008 can be installed on Vista, but is actually advising those who are still running Vista to install this one!?
Microsoft is not just admitting that updates for Server 2008 can be installed on Vista, but is actually advising those who are still running Vista to install this one!?  Caution: This update would definitely change your build number from 6.0.6002 to 6003, and personally I wouldn't install it unless my system was already fully updated to April 2019 (I did NOT mean to write "2017"). Caution: If you are using a legacy version of Avast, then you should uninstall it before updating your system because of a reported incompatibility. Update: It should then be possible to reinstall Avast/AVG products because Avast issued a micro-update.
Caution: This update would definitely change your build number from 6.0.6002 to 6003, and personally I wouldn't install it unless my system was already fully updated to April 2019 (I did NOT mean to write "2017"). Caution: If you are using a legacy version of Avast, then you should uninstall it before updating your system because of a reported incompatibility. Update: It should then be possible to reinstall Avast/AVG products because Avast issued a micro-update.
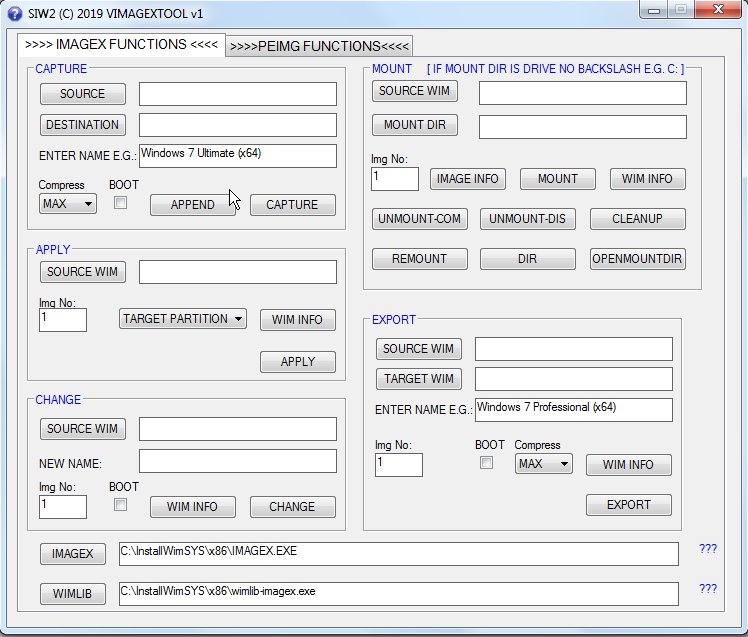
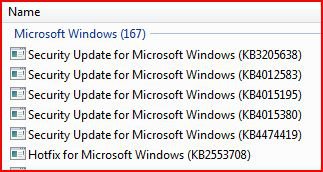
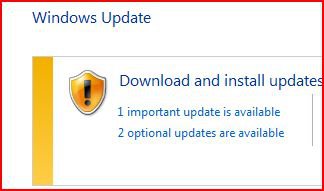
In other news, Microsoft has issued KB4474419 for SHA-2 code signing support for Windows 6.0. Third Edition: The KB article states, "There are no prerequisites for installing this update;" however 2019 SHA-2 Code Signing Support requirement for Windows and WSUS indicates that the April 2019 Servicing stack update for Windows Server 2008 SP2 (KB4493730) would also be needed for Windows updates. The experiment in post #2 therefore cannot be regarded as conclusive (I'm not even sure if Windows Update Agent 7.6.7600.256 was present).
 Furthermore, the KB article was updated yesterday (May 22), and contains this Notice: "This security update can be installed on Windows Server 2008 Service Pack 2 and on Windows Vista. "
Furthermore, the KB article was updated yesterday (May 22), and contains this Notice: "This security update can be installed on Windows Server 2008 Service Pack 2 and on Windows Vista. "  Microsoft is not just admitting that updates for Server 2008 can be installed on Vista, but is actually advising those who are still running Vista to install this one!?
Microsoft is not just admitting that updates for Server 2008 can be installed on Vista, but is actually advising those who are still running Vista to install this one!?  Caution: This update would definitely change your build number from 6.0.6002 to 6003, and personally I wouldn't install it unless my system was already fully updated to April 2019 (I did NOT mean to write "2017"). Caution: If you are using a legacy version of Avast, then you should uninstall it before updating your system because of a reported incompatibility. Update: It should then be possible to reinstall Avast/AVG products because Avast issued a micro-update.
Caution: This update would definitely change your build number from 6.0.6002 to 6003, and personally I wouldn't install it unless my system was already fully updated to April 2019 (I did NOT mean to write "2017"). Caution: If you are using a legacy version of Avast, then you should uninstall it before updating your system because of a reported incompatibility. Update: It should then be possible to reinstall Avast/AVG products because Avast issued a micro-update.In other news, Microsoft has issued KB4474419 for SHA-2 code signing support for Windows 6.0. Third Edition: The KB article states, "There are no prerequisites for installing this update;" however 2019 SHA-2 Code Signing Support requirement for Windows and WSUS indicates that the April 2019 Servicing stack update for Windows Server 2008 SP2 (KB4493730) would also be needed for Windows updates. The experiment in post #2 therefore cannot be regarded as conclusive (I'm not even sure if Windows Update Agent 7.6.7600.256 was present).
Last edited:
My Computer
System One
-
- Operating System
- Vista Home Premium x86 SP2
- Manufacturer/Model
- HP Pavilion Elite m9150f
- CPU
- Intel Q6600
- Memory
- 3 GB
- Graphics card(s)
- NVIDIA GeForce 8500 GT

 V86-v4.iso
V86-v4.iso