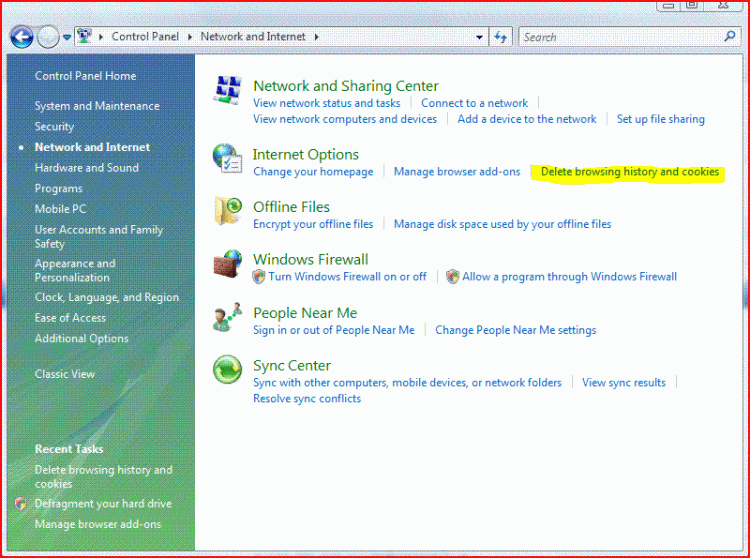
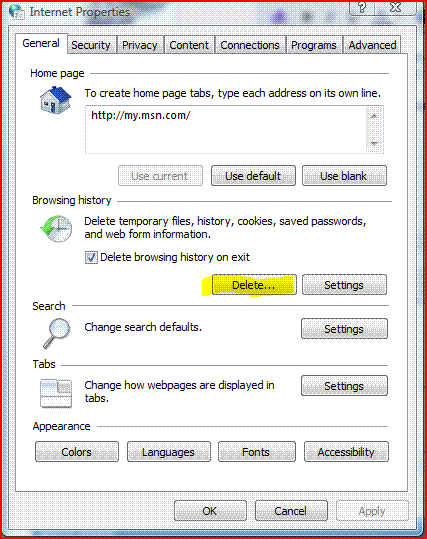
Source:
PE_VIRUT.ASA - Technical details
Arrival, Installation and Autostart Technique
This file infector may be downloaded unknowingly by a user when visiting malicious Web sites.
It creates the following registry entry to bypass the Windows Firewall:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\
SharedAccess\Parameters\FirewallPolicy\StandardProfile\
AuthorizedApplications\List
\??\%System%\winlogon.exe = "\??\%System%\winlogon.exe:*:enabled:@shell32.dll,-1"
File Infection
It hooks the following APIs so that when any of these APIs are called, it proceeds to its infection routine:
- NtCreateFile
- NtOpenFile
- NtOpenProcess
- NtCreateProcessEx
This file infector infects by appending its code to target host files. It infects files of the following types:
It does not infect files that contain the following strings in their file names:
Backdoor Capabilities
It searches for the
Winlogon process by enumerating the running processes and injects a thread that is responsible for its backdoor routines.
It connects to the following IRC server
irc.zief.pl and waits for a command from a remote user. Using this connection, it downloads
TROJ_INJECTOR.AR from the following URL: